from cedric@lemmy.ml to security@lemmy.ml on 12 Jan 2026 22:18
https://lemmy.ml/post/41605745
Introduction
This vulnerability report has been generated using data aggregated on Vulnerability-Lookup, with contributions from the platform’s community.
It highlights the most frequently mentioned vulnerability for December 2025, based on sightings collected from various sources, including MISP, Exploit-DB, Bluesky, Mastodon, GitHub Gists, The Shadowserver Foundation, Nuclei, SPLOITUS, Metasploit, and more. For further details, please visit this page.
A new section dedicated to detection rules is available.
The Month at a Glance
December 2025 was dominated by a massive surge in activity surrounding CVE-2025-55182 affecting Meta’s react-server-dom-webpack. With 852 sightings, this critical vulnerability (referenced by contributors as “React2Shell”) significantly outpaced all other vulnerabilities, highlighting a major focus on web application infrastructure exploitation.
Database and network security were also primary themes this month. MongoDB (CVE-2025-14847) ranked second in sightings and was added to the CISA Known Exploited Vulnerabilities (KEV) catalog on December 29th. The networking sector remained volatile, with critical vulnerabilities in Cisco Secure Email, WatchGuard Fireware OS, Fortinet, and SonicWall appearing in both the top sightings and the CISA KEV list.
Despite the influx of 2025 vulnerabilities, “zombie” vulnerabilities continue to plague the internet. Legacy issues from 2015 (D-Link) and 2017 (Zyxel) persist in the Top 10, proving that unpatched IoT devices remain active attack vectors years after disclosure.
In the broader ecosystem, CISA added a wide variety of threats to their catalog, ranging from mobile operating systems (iOS, Android) and browsers (Chrome) to desktop utilities like WinRAR. Additionally, community contributors highlighted significant structural shifts, notably the End-of-Life status for the Linux 5.4 kernel and new cryptographic implementation flaws in GnuPG.
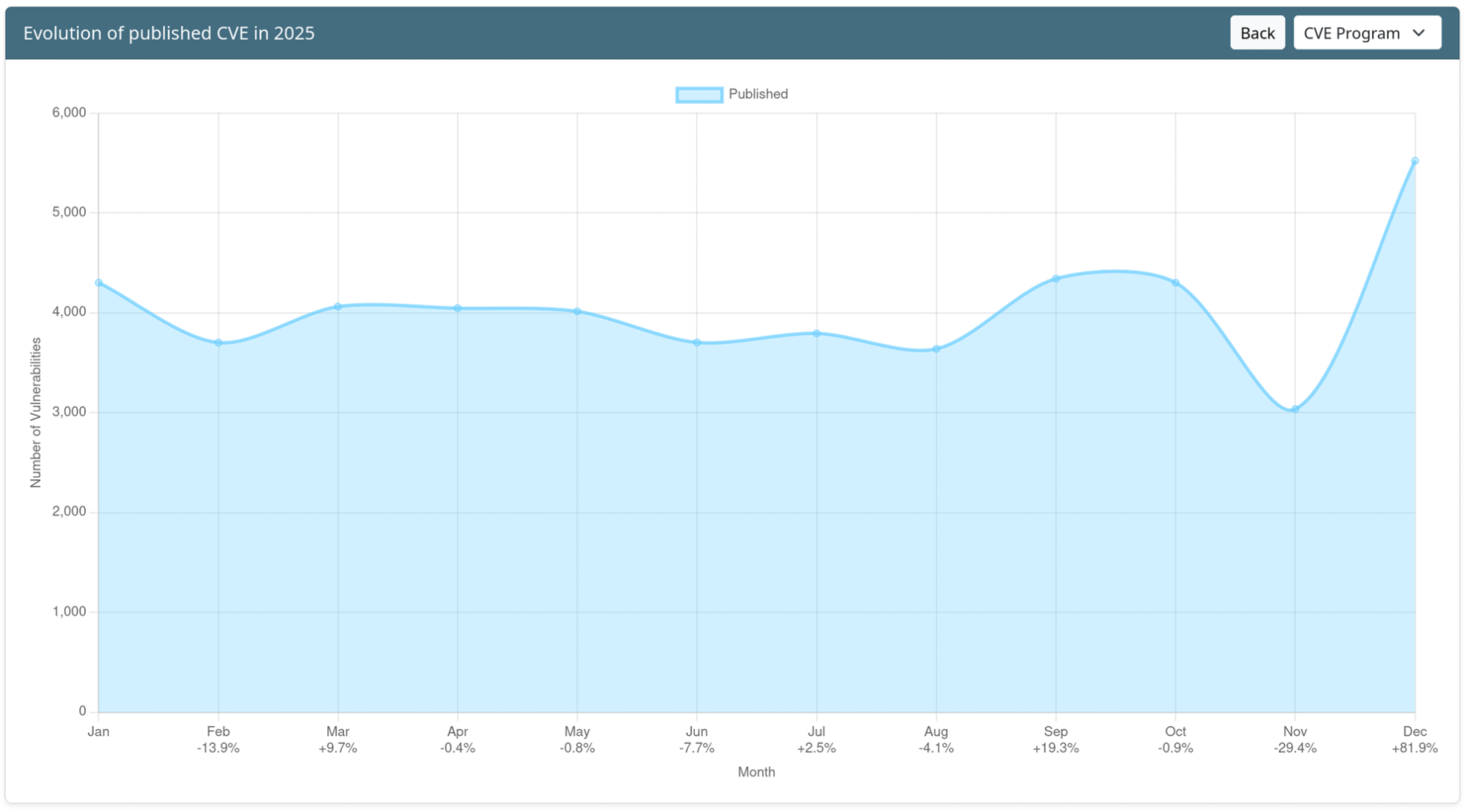
Evolution of published CVE in 2025
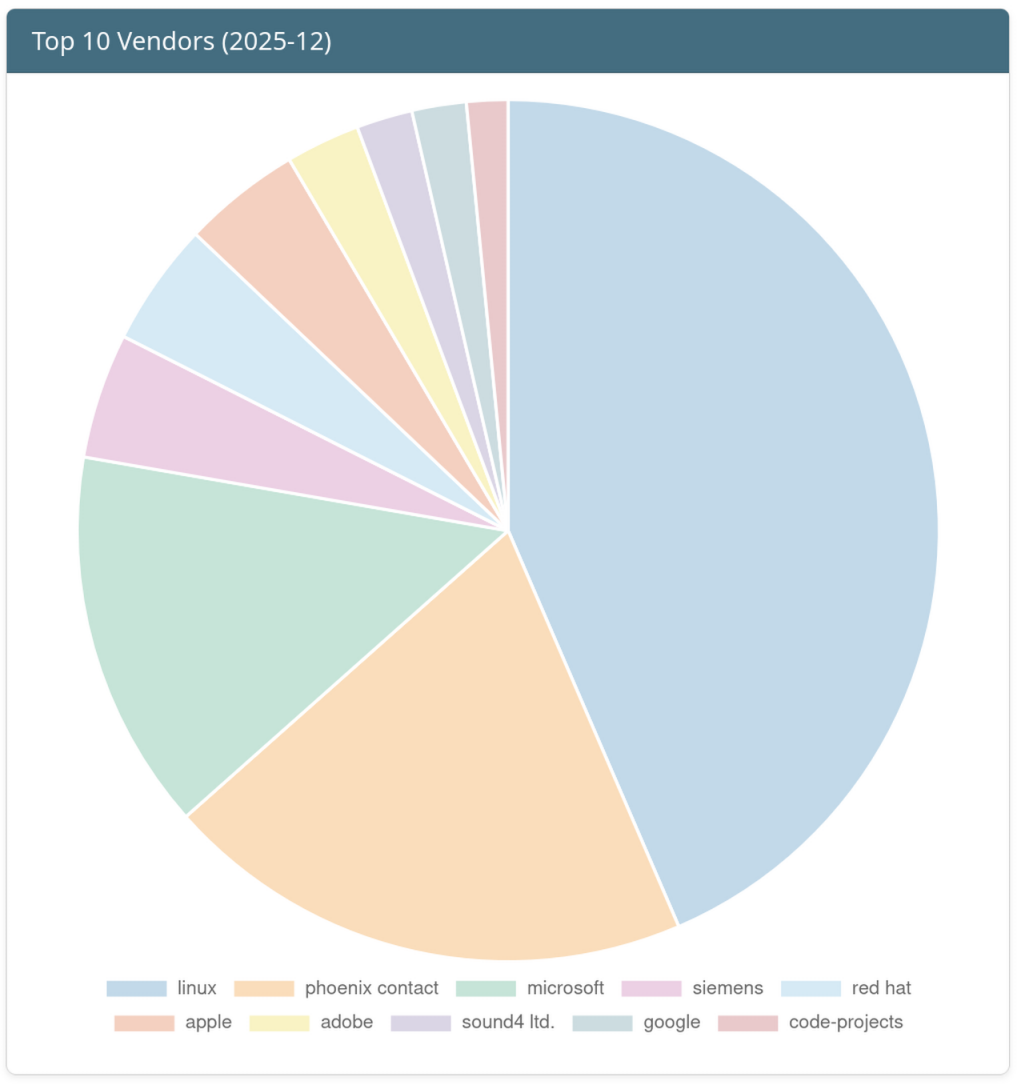
Top 10 Vendors of the Month
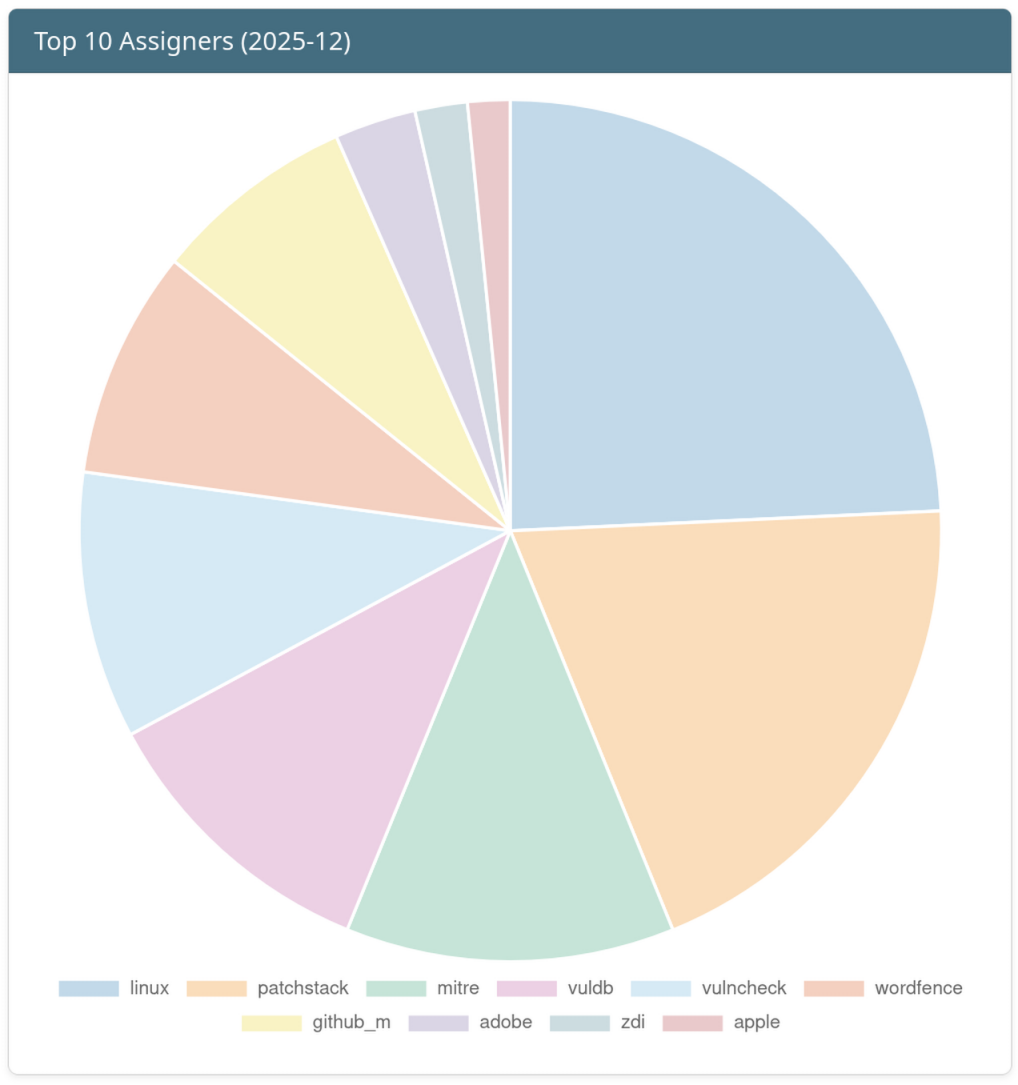
Top 10 Assigners of the Month
Top 10 vulnerabilities of the Month
| Vulnerability | Sighting Count | Vendor | Product | VLAI Severity |
|---|---|---|---|---|
| CVE-2025-55182 | 852 | Meta | react-server-dom-webpack | Critical (confidence: 0.9783) |
| CVE-2025-14847 | 204 | MongoDB Inc. | MongoDB Server | High (confidence: 0.9538) |
| CVE-2025-20393 | 89 | Cisco | Cisco Secure Email | Critical (confidence: 0.5137) |
| CVE-2015-2051 | 62 | dlink | dir-645 | High (confidence: 0.607) |
| CVE-2017-18368 | 62 | zyxel | p660hn-t1a_v1 | Critical (confidence: 0.9763) |
| CVE-2025-14733 | 60 | WatchGuard | Fireware OS | Critical (confidence: 0.976) |
| CVE-2025-66516 | 57 | Apache Software Foundation | Apache Tika core | High (confidence: 0.8155) |
| CVE-2018-10562 | 56 | dasannetworks | gpon_router | Critical (confidence: 0.9815) |
| CVE-2025-40602 | 53 | SonicWall | SMA1000 | Medium (confidence: 0.9162) |
| CVE-2025-59718 | 53 | Fortinet | FortiSwitchManager | Critical (confidence: 0.7339) |
Known Exploited Vulnerabilities
New entries have been added to major Known Exploited Vulnerabilities catalogs.
CISA
| CVE ID | Date Added | Vendor | Product | VLAI Severity |
|---|---|---|---|---|
| CVE-2025-14847 | 29/12/25 | MongoDB Inc. | MongoDB Server | High (confidence: 0.9538) |
| CVE-2023-52163 | 22/12/25 | digiever | ds-2105_pro | High (confidence: 0.9141) |
| CVE-2025-14733 | 19/12/25 | WatchGuard | Fireware OS | Critical (confidence: 0.976) |
| CVE-2025-20393 | 17/12/25 | Cisco | Cisco Secure Email | Critical (confidence: 0.5137) |
| CVE-2025-40602 | 17/12/25 | SonicWall | SMA1000 | Medium (confidence: 0.9162) |
| CVE-2025-59374 | 17/12/25 | ASUS | live update | Critical (confidence: 0.7584) |
| CVE-2025-59718 | 16/12/25 | Fortinet | FortiSwitchManager | Critical (confidence: 0.7339) |
| CVE-2025-43529 | 15/12/25 | Apple | iOS and iPadOS | High (confidence: 0.9918) |
| CVE-2025-14611 | 15/12/25 | Gladinet | CentreStack and TrioFox | High (confidence: 0.8669) |
| CVE-2025-14174 | 12/12/25 | Chrome | High (confidence: 0.8175) | |
| CVE-2018-4063 | 12/12/25 | sierrawireless | aleos | High (confidence: 0.7137) |
| CVE-2025-58360 | 11/12/25 | geoserver | geoserver | High (confidence: 0.5288) |
| CVE-2025-62221 | 09/12/25 | Microsoft | Windows 10 Version 1809 | High (confidence: 0.9943) |
| CVE-2025-6218 | 09/12/25 | RARLAB | WinRAR | High (confidence: 0.9977) |
| CVE-2025-66644 | 08/12/25 | Array Networks | ArrayOS AG | High (confidence: 0.8361) |
| CVE-2022-37055 | 08/12/25 | dlink | go-rt-ac750 | Critical (confidence: 0.9698) |
| CVE-2025-55182 | 05/12/25 | Meta | react-server-dom-webpack | Critical (confidence: 0.9783) |
| CVE-2021-26828 | 03/12/25 | scadabr | scadabr | High (confidence: 0.7378) |
| CVE-2025-48633 | 02/12/25 | Android | High (confidence: 0.8796) | |
| CVE-2025-48572 | 02/12/25 | Android | High (confidence: 0.9629) |
ENISA
No new entry in December.
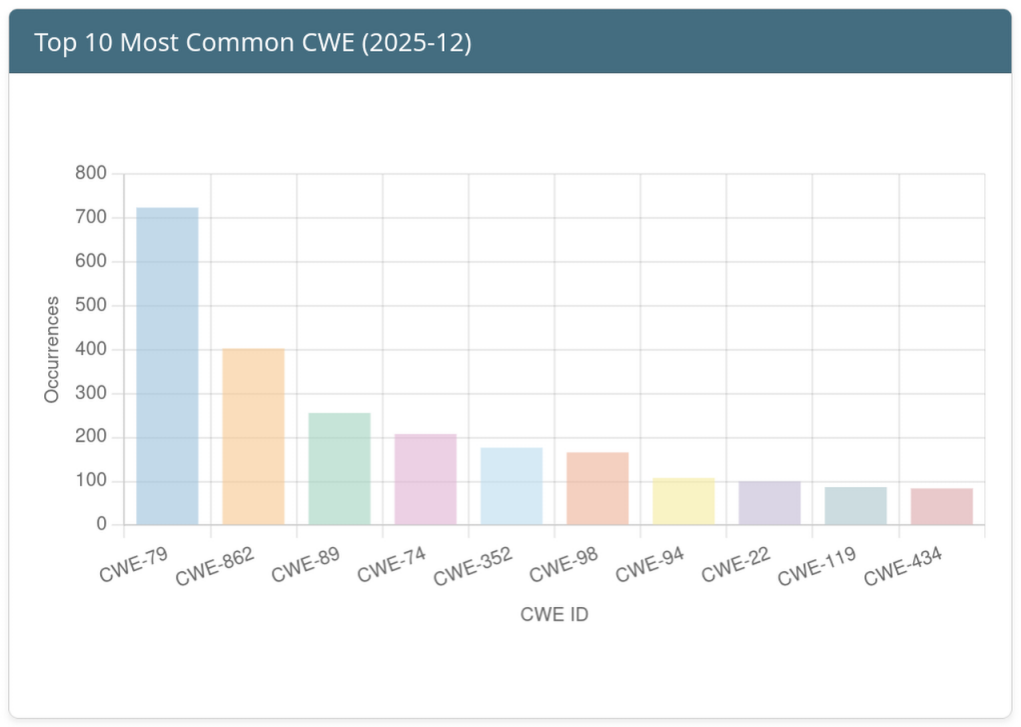
Top 10 Weaknesses of the Month
Detection rules
CVE-2025-55182
- ET WEB_SPECIFIC_APPS Waku RSC React2Shell Unsafe Flight Protocol Property Access [SURICATA]
- ET WEB_SPECIFIC_APPS Vite RSC React2Shell Unsafe Flight Protocol Property Access [SURICATA]
- ET WEB_SPECIFIC_APPS React Server Components React2Shell Unsafe Flight Protocol Property Access [SURICATA]
CVE-2015-2051
CVE-2017-18368
- ET EXPLOIT Possible ZyXEL P660HN-T v1 RCE [SURICATA]
CVE-2025-66516
CVE-2023-52163
- ET WEB_SPECIFIC_APPS DigiEver DS-2105 Pro time_tzsetup.cgi ntp Parameter Command Injection Attempt [SURICATA]
CVE reserved, but partial information has already appeared on the public internet
Sightings detected between 2025-12-01 and 2025-12-31 that are associated with vulnerabilities without public records.
Insights from Contributors
- gpg.fail - multiple vulnerabilities in GnuPG
- React2Shell
- The LAST Linux 5.4.y release. It is now end-of-life and should not be > used by anyone, anymore.
- Apache Tika
- Security content of iOS 26.2 and iPadOS 26.2
- Reports About Cyberattacks Against Cisco Secure Email Gateway And Cisco Secure Email and Web Manage
Thank you
Thank you to all the contributors and our diverse sources!
If you want to contribute to the next report, you can create your account.
Feedback and Support
If you have suggestions, please feel free to open a ticket on our GitHub repository. Your feedback is invaluable to us!
github.com/vulnerability-lookup/…/issues/
Funding

The main objective of Federated European Team for Threat Analysis (FETTA) is improvement of Cyber Threat Intelligence (CTI) products available to the public and private sector in Poland, Luxembourg, and the European Union as a whole.
Developing actionable CTI products (reports, indicators, etc) is a complex task and requires an in-depth understanding of the threat landscape and the ability to analyse and interpret large amounts of data. Many SOCs and CSIRTs build their capabilities in this area independently, leading to a fragmented approach and duplication of work.
The Computer Incident Response Center Luxembourg (CIRCL) is a government-driven initiative designed to provide a systematic response facility to computer security threats and incidents. The organization brings to the table its extensive experience in cybersecurity incident management, threat intelligence, and proactive response strategies. With a strong background in developing innovative open source cybersecurity tools and solutions, CIRCL’s contribution to the FETTA project is instrumental in achieving enhanced collaboration and intelligence sharing across Europe.
threaded - newest