Prusa Printers Firewall Logs
from 7toed@midwest.social to privacy@lemmy.ml on 22 Dec 2025 07:39
https://midwest.social/post/40656980
from 7toed@midwest.social to privacy@lemmy.ml on 22 Dec 2025 07:39
https://midwest.social/post/40656980
I tried searching for answers as to why these machines are reaching out to numerous locations despite not using PrusaConnect. Location lookup returns the expected Czech, as well as location across the US. I recently also set a friend up with with an Elegoo printer and that was expectedly noisy as hell, but I was surprised with Prusa being the ‘privacy pick’.
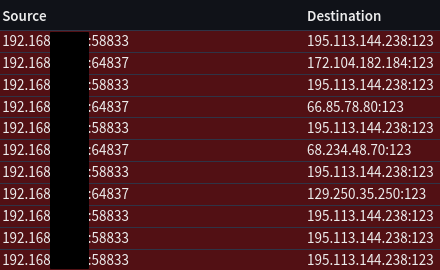
For those curious, here’s the logs since about midnight, it seemingly doesn’t talk during the day.
209.51.161.238:123 195.113.144.238:123 23.150.41.122:123 193.29.63.226:123 162.244.81.139:123 64.246.132.14:123 172.104.182.184:123 66.85.78.80:123 68.234.48.70:123 129.250.35.250:123
Edit: Midnight brain forgot what ports are for, and that is for NTP, thanks yall
threaded - newest
123 is NTP, used for time synchronisation. Often a pool of servers is used.
Bang on. Something is trying to update its clock.
OP, I suggest you ok that traffic, but if you want to lock it down allow *.pool.ntp.org and *.(Your country prefix).pool.ntp.org
www.ntppool.org/en/
Again, what would a printer need a clock for?
If it’s a multifunction, printing the time/date on the fax.
It is a 3D printer
To show the expected completion time of the print.
A 4D printer would need to know the time.
Ofcours, to print time
Anything that connects to the network needs a synchronized clock with other devices it directly communicates with in order to make sure it’s not being subjected to timing attacks. This has been standard practice for 25 years, maybe more, in the end user world because some high profile computer screw ups made use of it. People with weird systems, off the gridders of olde and ppl still on dial up in the teens had some interesting problems to solve when generally all ISPs got drug kicking and screaming to the table by os updates that made synchronized clocks a non negotiable requirement.
Please explain what kind of timing attacks because what you wrote doesn’t make sense in the context of a damn printer.
Server? Sure. Printer? Why can it even access public internet?
I’m not sure why you think any digital device shouldn’t know what time it is. It’s not leaking any kind of personal information, just literal facts about reality.
Maintaining a shared “now” is actually an interesting problem from a relativistic point of view, considering you need time to communicate what time it is. NTP is a relatively simple protocol with some clever tricks around latency; it is organized by strata which go from very precise, authoritative sources (these are atomic clocks at universities, not the NSA) to various levels of “mirrors”, down to within your LAN. It is massively distributed and decentralized by nature, to be able to handle everyone to be in sync without overwhelming a handful of primary clocks.
The end device does not need to be able to talk to the internet at all, just to your router (or designated NTP server if you’re into that). It is such an old protocol that it is embedded in most consumer routers, and getting a server running in Linux is literally just install, start. You don’t need to connect upstream at all, you can absolutely say “on this network I am the god-clock”.
My challenge isn’t about NTP but about printer shouldn’t be able to communicate with the internet, as it has no need for it.
You said: It’s common.
Okay, cool. So is cancer.
Exactly! So why allow the printer to go past it!
Well yeah, me needing to lock down this network properly is why I ran up on this, but also being someone who hates reseting the stove clock after a power out, I wouldn’t bat my eye at NTP requests really.
The types of attacks can be mischaracterized as “race conditions but over the network”. Theres about forty years of history here and it’s way more complicated so unless you really wanna get into it I’ll leave it there.
The printer doesn’t know if it’s plugged into a private network or is internet facing. Timing attacks can occur on private networks as well as on the internet. Having accurate utc is almost always a prerequisite for communicating with other devices.
Therefore, the printer needs to know what time it is. It does this through ntp on port 123 just like phones, computers and network connected paper and ink printers do.
Me: please explain what kinds of timing attacks can affect a printer and what are the consequences, because I can’t think of any
You: Timing attacks. They are old. They are bad. Therefore printer needs to be protected from them.
I don’t think you answered my question.
Well, one example of a timing attack is replaying. It’s a fucking classic, chefs kiss kind of signaling attack where you bypass the need to understand what’s going on by just saying it verbatim using your capacity to accurately reproduce some information, easily sidestepping all kinds of shibboleths.
Before computers replaying was used during both ww1 and ww2 to confuse and misdirect radio operators and back when keyless entry was a newfangled thing it was used to spoof the unique signals each manufacturer chose to use. Even after they all switched to rolling codes, replaying is a way to both desynchronize the owners fob and replay their command at almost the same time, getting you into the car.
In computing, replaying would be a fantastic way for a man in the middle to pretend like he knew some password or was some service, indicated by an encrypted or hashed transmission the man in the middle could just store and replay. Darla can listen in to the way alfalfa says the password to the he man woman haters club and with good practice, recite it convincingly!
If Darla were a computer then even alfalfas securely hashed password would be no problem because she doesn’t need to pronounce it, but just reproduce it in all its unpronounceable hexadecimal glory.
But if the instructions for the he man woman haters club authentication was instead an encrypted transmission saying “the clubs clock says it’s 4:15.45.6789 pm April twentieth 1969. When you reply with your password hash, include the clubs clock time down to the millisecond.” Now Darla can’t just replay alfalfas hashed authentication token because it’s the wrong time!
Because of ntp, girls remain not allowed.
How would such an attack affect the printer? Who can say! I can speculate that an interloper could make it do things the user could, like print stuff, burn up the nozzle or smash into its extents. The printer controller is basically just a little computer so gaining access to it as an authenticated user might make it easier to escalate privileges and use it like any other computer might be used by a malicious actor as well.
Let’s say though, that part of the out of the box setup is connecting to the printer through some app or program. You want encrypted tls for that and you want the user or their software to exchange certificates to make it all official, but that technology requires that time be synchronized between the two devices in order to do so. If the printer has inaccurate enough time it can’t even negotiate a secure connection with the owners phone app they use to send it instructions.
So ntp makes sense in this case. If you’re gonna be doing communication you gotta do it responsibly and it’s good that iot stuff like this is making some effort!
E: I realized I glossed over some stuff assuming you’d make some jumps and in the cold light of morning that might not actually be the case.
Uhh, let me be clear: what is much closer to reality is that the guard doesn’t assert the clubs clock time but instead relies on all parties knowledge of utc (gmt but long and made by fat people) and there’s a snappy little back and forth between Darla and the door guard at the hmwhc where Darla asserts her systems time a few times and the door guard is able to use that to reasonably expect what a hashed token containing her understanding of the current time could be off by.
Now when she tries to pass alfalfas hashed password and current time token she fails because it doesn’t match her expected time or the door guards and there’s even possibly a record of who asserted and when, giving a forensic chain that can be used in legal proceedings against women!
Hashing is exactly what it sounds like, but math. Just like at the breakfast spot, it’s when you take your easily recognizable potato with the word “formosissima” carved into it and cut it into a bunch of equally sized pieces. It’s still all there, just made into a hash! If someone knew exactly your cutting process they could put the tater back together and have a big ol meltdown over it.
That simple system where you figure out how incapable of telling time your unknown, untrustworthy weirdo attempting to gain access to some resource is, then expect them to cough up a token that contains hashes of both that resources shared secret and the time and then check em out to make sure they’re reasonable is a super straightforward way to implement the “actually look at the id being presented at the bar” test in computers.
This is so widespread that you can’t do credit card transactions without it, can’t establish secure http connections to websites without it and most certainly can’t responsibly pass credentials back and forth without it.
But why would that be required if the printer is only on the local network? Because we can’t t
I just want you to know I read and appreciated your comment. I’m very glad my naiive latenight post about NTP ended up making some pretty interesting content for people learning privacy basics
What printer are you using? I have a h frame knockoff of one from the pre covid days but need to get a resin.
The elegoo saturn 4 ultra is what I got, been filamenting for years but new to resin. I’ve finished about a dozen prints, stupid easy to get going with its autoleveling. It did lock up completely and failed the job seemingly after i firewalled it, but hasn’t repeated since. The quality is immaculate, printed a 4 inch tall Sears tower and its got every little antenna. Though the slicer wasn’t playing with wine, so I needed to use a windows VM unfortunately
Do you have a 12k or 16k one?
16k, might as well go all the way
Or spin up your own NTP server and NAT those requests to it.
Why would a printer need time? The only think that cames to mind is freezing cartridges after x months.
Probably some legit uses eg direct from file prints with filename and timestamp, but also there’s the yellow tracking dots: en.wikipedia.org/wiki/Printer_tracking_dots
Printer isn’t responsible for timestamps on your document. If that would be regarding tracking dots, then block it anyway, right? And if it’s a 3d printer then it still doesn’t need to have correct synchronized time, it only needs to be able to count how the time passes.
Prusa is a 3d printer. It can be to show the date, check the validity of certificates, show in logs, or just tell you when your print will be done.
AFAIK the firmware is open source so ultimately you can look exactly what it does with it. Same as any Linux system, really.
You want any device that does crypto (like verifying a certificate) to have a synchronized clock.
Huh thank you. Now its not like I already have my own NTP instance that I seemingly don’t have the option on the printers for… not sure why I didn’t to look at the destination port frankly 🤷♂️
You can put the time server in your DHCP offer. No idea if the printer will use that, but it’s worth a shot.
Haha now I feel like I overreacted. That mentioned Elegoo printer had me on edge, 100s of https requests per minute without an attached account even. Time to tidy up my services more and see if I can point them at my own ntp
No idea about the connections but did you just censor your local IP address??
Good opsec, really.
Edit: also I just realized this is the Privacy community lol
.
I was taught in my IT Sec classes to avoid sharing any unnecessary information. Information on private IPs can be used to better understand your network, allowing a threat actor to better navigate your network without needing to do ip scans (which are very obvious and should trigger even basic detection). While it is most likely pointless (since OP probably isnt at risk of targeted attacks), it is still good opsec.
.
Call it performative, but you don’t know what subnet they’re on 😝
.
I’m sorry for upsetting you so much. I don’t think I said I defeated surveillance so that’s on you.
While right, what fun is it using enterprise grade hardware if you’re not at least going to pretend to be serious with it 😁
I mean, basically any device will send a DHCPDISCOVER broadcast on 255 when it connects, to see if there is a DHCP server on the network. Unless you’re running your entire network on pre-configured static addresses and have your router set up to intercept all broadcast messages (and treat the broadcasting device as hostile), any device plugging into the network would automatically broadcast a message anyways.
And honestly, if you’re being that paranoid about your network, you’d probably be better off just using port security and a MAC whitelist instead. It would save you a lot of time with manually configuring IP addresses. That way any threat actor would only be able to connect if they already knew a whitelisted MAC. And gentle device discovery can also be automated without obvious brute force “ping every IP in the subnet at the same time, and blatantly scan common ports on responding IPs” network scans. They’ll take longer, (and passive scans may miss some devices) but they wouldn’t trip the rudimentary “watch for any device firing ping requests out to every single IP” scan detection. Passive scans can be particularly difficult to detect.
Just block ICMP lol /s
The point of my comment wasn’t that OP was in “real danger” if they showed local IPs, just that it doesn’t hurt to censor them. Never give more information than necessary. I censor usernames and filepaths on any screenshots of the terminal, even though if an actor has the kind of access to utilize that information I am probably already fucked. I think it is good practice to always scrutinize the information you give out willingly.
How much metadata do you need until its PII? What subnets exist and which devices are potentially leverageable are valid points in a threat model… maybe not entirely suited for everyone but I’m sure as hell my employer is unknowingly greatful for
.
How do you know mine isn’t not 192.168.2.1 HMMM?
You’re kinda right, but PII != bits of entropy about you
Yep this is just NTP, nothing nefarious. If you have a “good” router that has an NTP server and can set the related DHCP option, try setting that. The servers it uses might be hardcoded, but I believe it will honor the DHCP lease.
Well shucks you inadvertantly helped me with a couple other backburner issues, thanks!
Prusa recently partnered with an Israeli company called Fillament2 during the genocide so you already know what’s up.
What is up?
FUCK I need my own printer with blackjack and hookers
Ender 3 Pro since it literally can’t connect to anything on its own?
IDK man the noises they make may communicate to the israeli bird drones
And Klipper
Now I want to usurp NTP server IP addresses on my local network to send my local printer back in the 70’s. You should have accept B&W printing without those color cartridge, toaster !