Google Spoofed Via DKIM Replay Attack | EasyDMARC
(easydmarc.com)
from Der_Fossyler@feddit.org to privacy@lemmy.ml on 26 Jul 2025 13:47
https://feddit.org/post/16328027
from Der_Fossyler@feddit.org to privacy@lemmy.ml on 26 Jul 2025 13:47
https://feddit.org/post/16328027
cross-posted from: feddit.org/post/16327978
threaded - newest
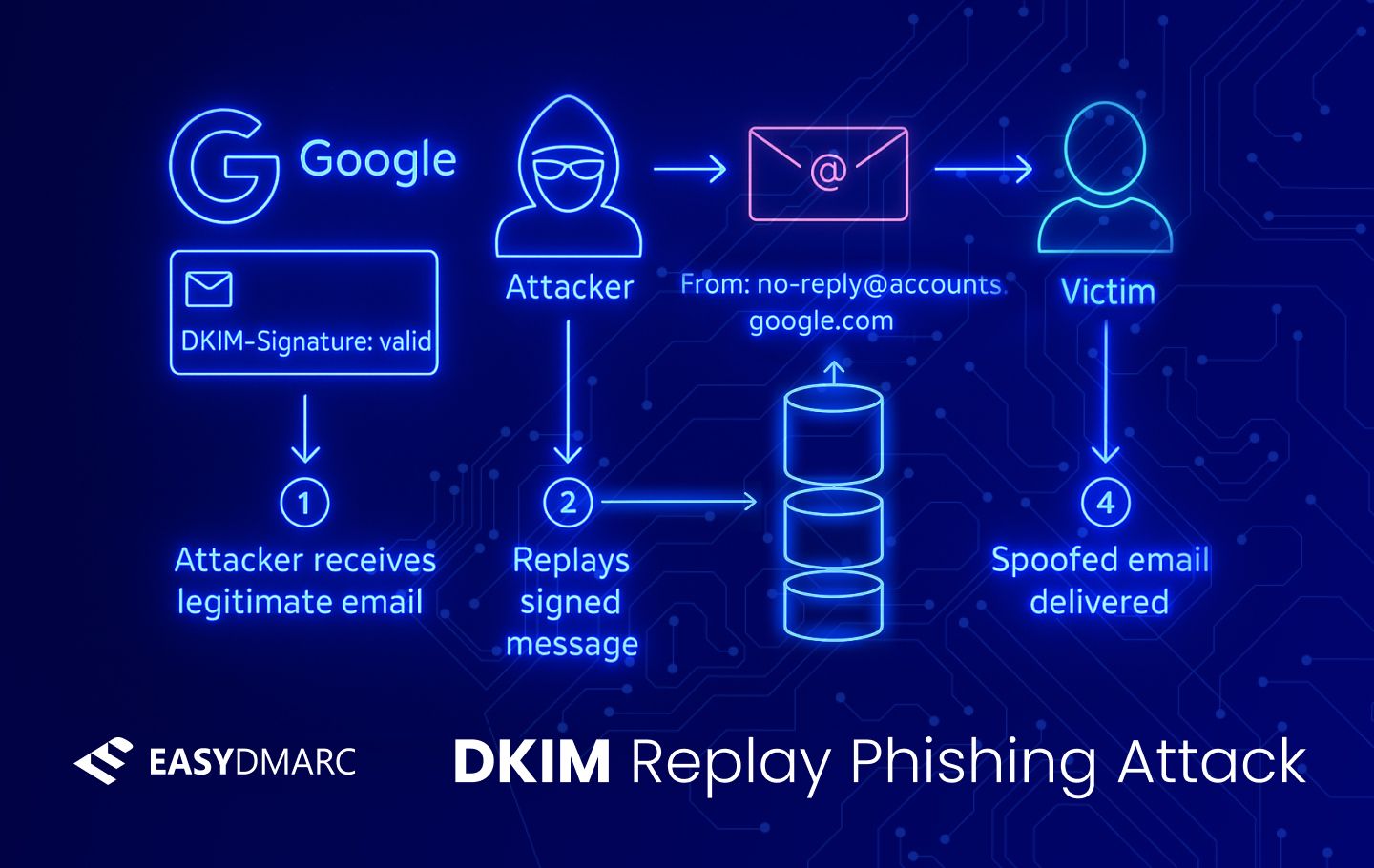
They found a way to inject text into a google email notification (by setting the name of their google workspace account to the phishing message), and then set up a mail forwarding service to redirect the notification to the victim accounts. That way the victims receive a legit email from google but the text of the email is attacker-controlled and can point the victim to their phishing site.
It’s not really a vulnerability in DKIM. The bug is in google’s use of attacker-controlled text fields in their notification emails.
I saw one of these recently, too, with Microsoft. Someone opened a 365 tenant and set the name of the tenant to “Thank you for your purchase of Microsoft Defender for $509.99. If you have any questions, please call [attacker controlled number]”
Then they set their exchange online to forward messages to the intended victim, and requested a password reset email. So the victim ended up receiving an email that came from microsoftonline.com that said “Your password has been successfully changed. Thank you, [scam text]”