Why does my pc make so many connections?
from Clark@lemmy.ml to privacy@lemmy.ml on 03 Sep 15:56
https://lemmy.ml/post/35624422
from Clark@lemmy.ml to privacy@lemmy.ml on 03 Sep 15:56
https://lemmy.ml/post/35624422
Hello all,
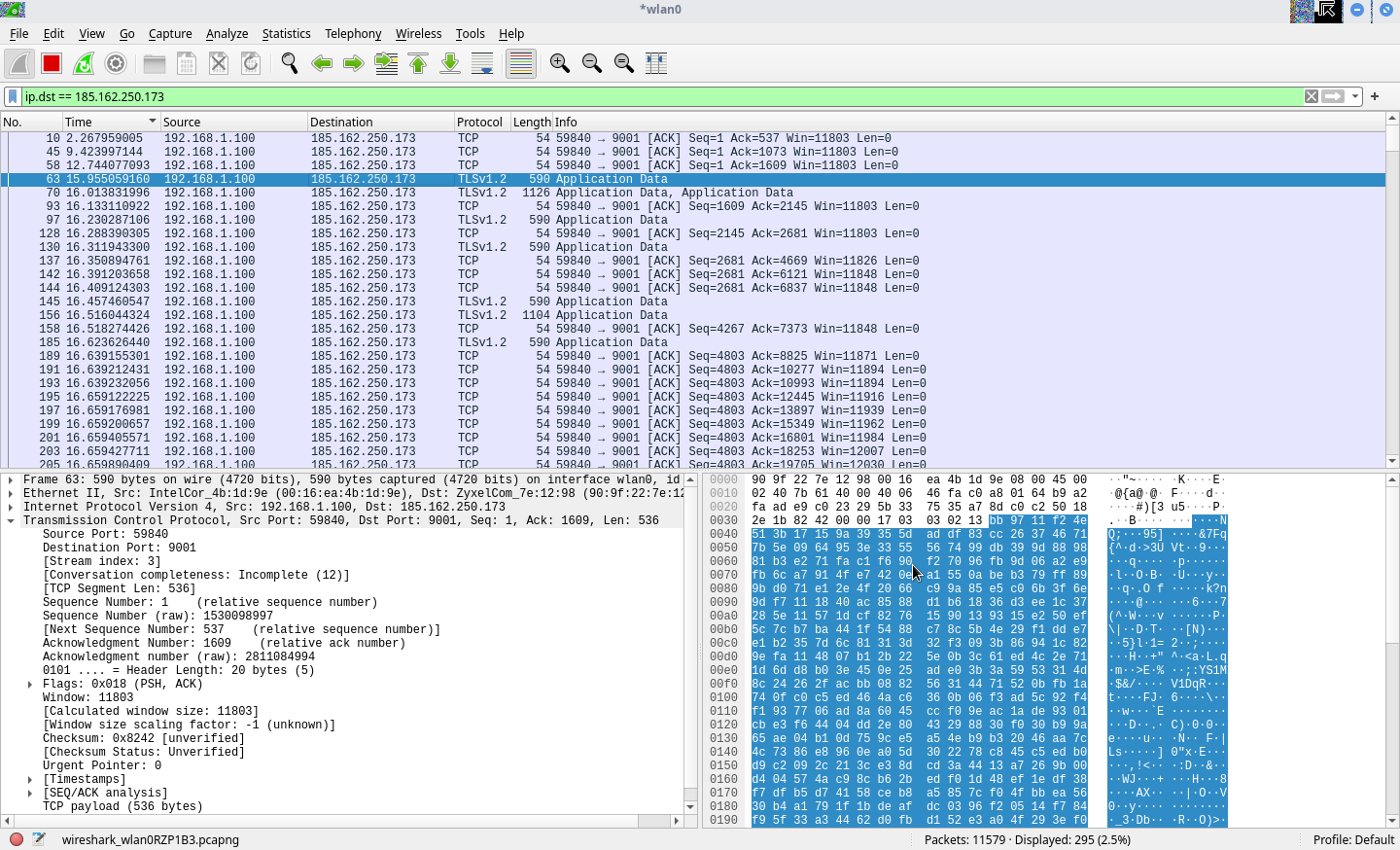
According to the Wireshark record my computer connects to various services often, including Amazon, Hetzner, 1337 Services GmbH, Evanzo GmbH and ThomasFamilyInvestments. The most often were the connections to mail.my-mail.rocks which is a part of Netcup GmbH. I have a somewhat minimal distro and the attached recordings were made when no app was open including no browser. I can send the other screenshots showing other connections too. I’m suspecting of malware since some time ago but can you help me clarify these connections please?
threaded - newest
Just open sudo ss -tulpn u will see all programs with opened port and u will killing disabling until u will find source of network noise
But without “l”. This connections created as client I think:
ss -tupn
i only have these over long term but brave was closed when recording:
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp ESTAB 0 0 192.168.1.100%wlan0:68 192.168.1.1:67 users:((“NetworkManager”,pid=1065,fd=27))
tcp ESTAB 0 0 192.168.1.100:57728 185.246.86.175:9001 users:((“tor”,pid=1143,fd=16))
tcp ESTAB 0 0 192.168.1.100:60406 54.36.178.108:443 users:((“brave”,pid=5153,fd=27))
tcp ESTAB 0 0 192.168.1.100:40606 89.58.56.112:587 users:((“tor”,pid=1143,fd=12))
If you are receiving data from tor, then you are most likely seeing these connections. They also change over time, so tor relay nodes change and can be located anywhere.
In addition, in the example you have port 9001, which means that relaying is most likely enabled in your client and you are a relay for other participants. Check the settings of the tor (relay/bridge).
Thanks for the informations. This clarifies a lot.
Also it seems that your browser is still active on your computer called brave?
No, it wasn’t at the time of recording. It was a confirmation later on that tor and network manager were the only apps using the ports with brave opened.
Do you have any apps open in the foreground or background while doing the packet capture? Check with top or htop and make sure all your apps are truly closed.
Amazon, Hetzner, and the others are VPS providers among other services, so seeing connections to those by apps could be fairly normal as they often check for updates or download supporting items to make the app work.
Thank you for the informations. There were nothing in the foreground but tor was apparently running in the background. But I’m still not sure if these services were all due to Tor. I need to run another record I guess
it sounds like you’ll need a better handle on what’s running on your computer.
if this matters to you enough: you can start with pruning the systemd services that are running to remove the ones you don’t want so that you can know for certain what is supposed to be running and then run another capture to see where it’s calling out to.
Tor creates a ton of connections to all kinds of places, so that might have been the source.
Per its nature, tor is definitely going to create a lot of noise in your capture. Shut it down and try again, see if you still have so many connections.
It is highly unlikely that you have malware that you can’t see, so if you still see them after shutting down tor, use tools that tell you which app has established connections.
Yeah, * Tor. Its primary job is to make and destroy tons of connections to keep you private.
Edit: Still getting used to FUTO keyboard. It doesn’t need me to say comma
.
That mail/[.]my-mail/[.]rocks maps to the tor network.
metrics.torproject.org/rs.html#details/E3F16EEB32…
so am i running a relay in the background although tor browser is closed?
If it’s like a vpn interface, it’s still running as a deamon in the background even if the browsers are closed.
Like others have said you can check what application is using each open port. You can also check running processes (ps | grep keywords) and interfaces (ip a).
That screenshot just looks like a computer (.100, is that you?) dialing the upstream device (a zyxel!), it doesn’t seem to show what the intended recipient is. If you’re running windows then the start menu ads do crazy stuff. Also I asked if that last local ip octet is you because wireshark will show you other computers traffic coming across its wireless interface.
From a high port to a low port makes me think it’s someone else on your network doing piracy.
Yes, .100 is me. I have a Zyxel router, should it show the intended recipient? I’m running Linux. What do you mean by a high port to a low port? I also think there is a malware.
If you think there’s malware then just wipe and reinstall.
If you wanna find out what the computer is connecting to, post the wireshark logs.
Amazon, hetzner and Evanzo are hosting providers, krebs seems to think 1337 services is a scammy site/company and thomas is a shell company. My-mail.rocks has some tor nodes.
Exactly my point. Just share the actual wireshark log. You record a few seconds and then stop. And then share the log.
I’m not just trying to get rid of the malware but also understand what it’s doing. Besides, wiping the system doesn’t help as some viruses can permanently corrupt bios. So before wiping out, I think it’s a good idea to know what’s going on my pc and where do my data go, if there is a malware. I’m a rookie with network monitoring, that’s why I’m trying to learn from more experienced users. Here is the part of the original capture: limewire.com/?referrer=pq7i8xx7p2. I will disable tor and close all apps along with some serviced and record again. I will let you know, thanks for your help
You will probably get better answers if you ask in a networking forum rather than u/privacy.
forum.level1techs.com
.
The answers are good enough for me here
I can’t see that link. Just drop the log in a paste bin or something.
You’re probably not in a position to figure out what the malware is doing, or even if you have malware running.
If you brought me your computer and said “I think I have malware and I want to understand what’s happening” I would remove the drive, image it using an appliance instead of a computer and put the image in a forensic environment so I could observe it safely.
I wish I could bring it to an expert. Do you know how to find one? Here is the file: paste.centos.org/view/5df16fbe Sorry for the delay
.
Because you’re on the internet
Does also your computer connect to Amazon, Hetzner, 1337 Services GmbH, Evanzo GmbH and ThomasFamilyInvestments without a reason?
Everything has a reason
Use bandwhich to see which programs are using traffic ;)
I will try it, thank you :)
I find wireshark too confusing unless you have a lot of experience with it.
It looks like you are using linux because I see Wlan0 at the top of the image
I use ss
ss --help
to see what you are connecting to
ss -x -a
ss -o state established
ss -o state established ‘( dport = :http or sport = :http )’
what processes are using open sockets
ss -pl
TCP sockets
ss -t -a
UDP sockets
ss -t -a
a deeper guide here:
cyberciti.biz/…/linux-investigate-sockets-network…
-ufor udp in the last one.SS is a weird name but ok.
Socket shark, maybe? The 2 digit namespace is valuable enough that there was no way
sswas going unused, nazi-association be damnedUse Portmaster
This is the way
Portmaster is mandatory nowadays, like also InviZible Pro in Android
Oooooo I haven’t seen that one before, thanks!